Group Provisioning
Group Provisioning Policies
Some applications have group create and update provisioning policy. Active Directory is one of them. New fields can be will added/removed in create/update group provisioning policy, then that field will be added/removed from ‘Object Properties’ tab. In this demo we will keep it simple and won’t add/remove new fields in group provisioning policy. We will take example of Active Directory to understand this. Active Directory has feature String “PROVISIOING” so it has capability to provision. Want to learn more about feature String click here
NOTE: The fields of create and update group policy appear in ‘Object Properties’ tab
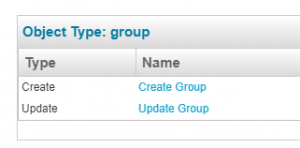
The fields present in create and update group policies can be seen in ‘Object Properties’ tab of entitlement catalog
Create Provisioning Policy
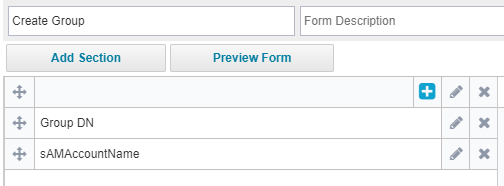
Below is Active Directory create group policy. By default, AD connector has Group DN and sAMAccountName fields are present in Group Create Provisioning Policy.
Update Policy
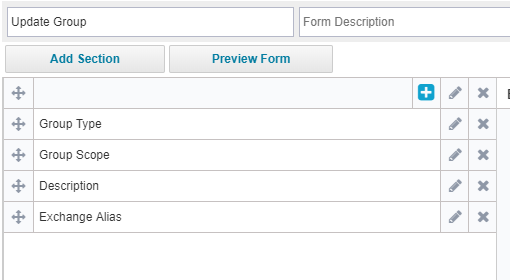
Below is Active Directory group update policy
Create Group from UI
To add a new Active Directory group through SaiPoint IIQ UI, Go to Entitlement Catalog -> ‘Add New Entitlement’ button.
Standard Properties
You have to select an ‘Application’ and then other highlighted fields
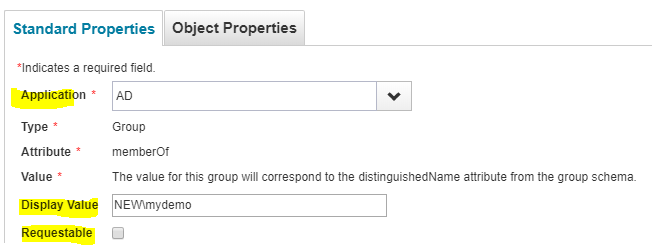
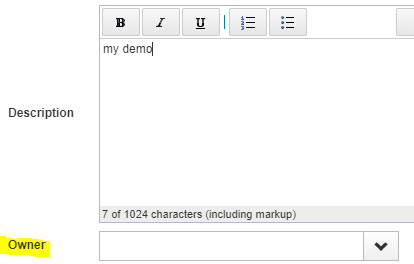
NOTE:
Owner field does not set the ‘managed by’ field in Active directory. This owner field is limited to Sailpoint.
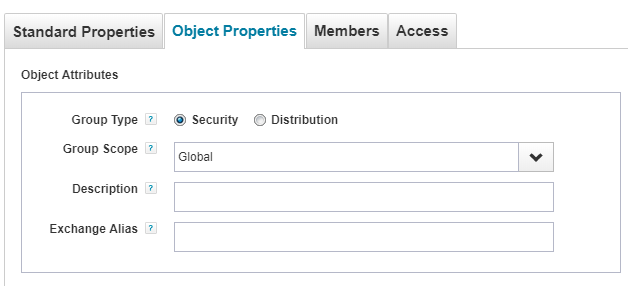
Object Properties
Notice that in object properties tab, all the fields and from both, create and update policies of group.
If you add/remove any field in create/update group provisioning policy, then that field will be added/removed from ‘Object Properties’ tab.
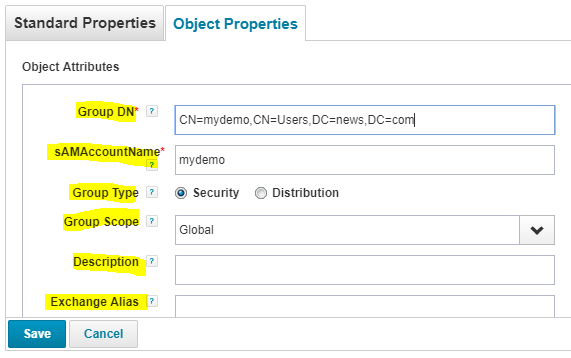
Click on save.
This will invoke a workflow, Entitlement Update. Which can be seen in Global settings>Identity IQ Settings>Miscellaneous
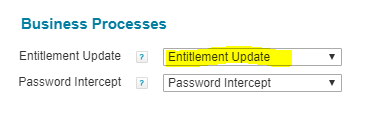
And you will see a message like below

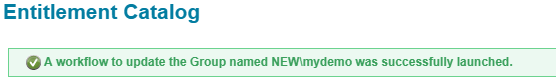
Provisioning Plan Created By IIQ
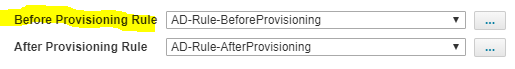
The plan created can be seen in before provisioning rule
<!DOCTYPE ProvisioningPlan PUBLIC “sailpoint.dtd” “sailpoint.dtd”>
<ProvisioningPlan targetIntegration=”AD” trackingId=”dff7a79e0c7845f385be3b74e6fa084b”>
<Attributes>
<Map>
<entry key=”requester” value=”spadmin”/>
<entry key=”source” value=”GroupManagement”/>
</Map>
</Attributes>
<ObjectRequest application=”AD” nativeIdentity=”CN=mydemo,CN=Users,DC=news,DC=com” op=”Create” type=”group”>
<AttributeRequest name=”distinguishedName” op=”Set” value=”CN=mydemo,CN=Users,DC=news,DC=com”/>
<AttributeRequest name=”sAMAccountName” op=”Set” value=”mydemo”/>
<AttributeRequest name=”GroupType” op=”Set” value=”Security”/>
<AttributeRequest name=”GroupScope” op=”Set” value=”Global”/>
</ObjectRequest>
<Requesters>
<Reference class=”sailpoint.object.Identity” id=”4028818766902596016690272ffc010b” name=”spadmin”/>
</Requesters>
</ProvisioningPlan>
Group Created
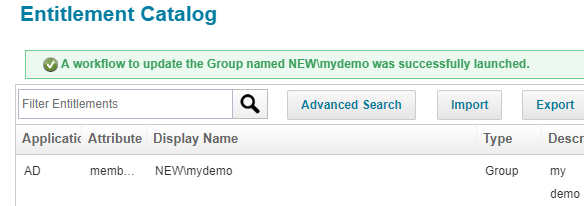
In SailPoint UI
In SailPoint UI, a new group has been created which you can check in entitlement catalog.
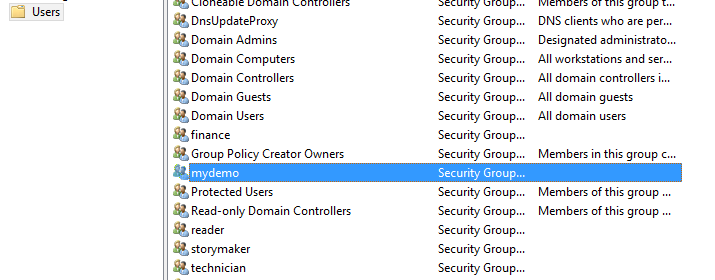
In AD UI
That group will also be in Active Directory which you can verify in Active Directory
Update Entitlements
You can edit an entitlement, you can update fields in ‘Object Properties’ tab. This will again trigger ‘Entitlement Update’ workflow and this form is presented from ‘update group’ provisioning policy of the application.
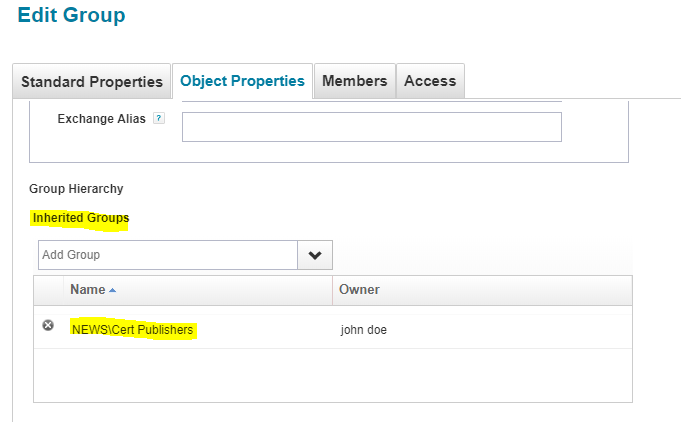
Provisioning Plan created by IIQ
Before provision Plan == <?xml version=’1.0′ encoding=’UTF-8′?>
<!DOCTYPE ProvisioningPlan PUBLIC “sailpoint.dtd” “sailpoint.dtd”>
<ProvisioningPlan targetIntegration=”AD” trackingId=”df3abcc68b4b4706935e84e617b94066″>
<Attributes>
<Map>
<entry key=”requester” value=”spadmin”/>
<entry key=”source” value=”GroupManagement”/>
</Map>
</Attributes>
<ObjectRequest application=”AD” nativeIdentity=”CN=mydemo,CN=Users,DC=news,DC=com” op=”Modify” type=”group”>
<AttributeRequest name=”memberOf” op=”Set” value=”CN=Cert Publishers,CN=Users,DC=news,DC=com”/>
</ObjectRequest>
<Requesters>
<Reference class=”sailpoint.object.Identity” id=”4028818766902596016690272ffc010b” name=”spadmin”/>
</Requesters>
</ProvisioningPlan>
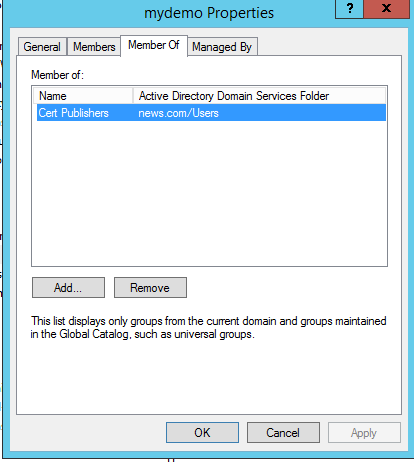
Here in above example ‘member of’ attribute is updated for the newly created group. The member of attribute of AD group is represented as ‘Inherited Groups’ in Sailpoint IIQ as shown and highlighted in above figure.
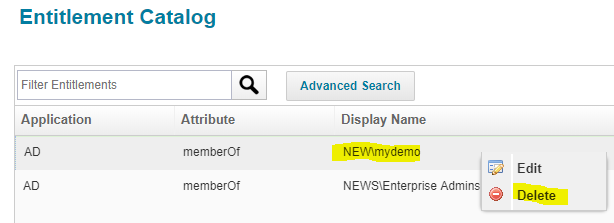
Delete Entitlement
Right Click on entitlement and click on delete to delete the entitlement
Provisioning Plan for delete By IIQ
<ProvisioningPlan targetIntegration=”AD” trackingId=”3f062c9c34c44bfd8d7297efefc3b7f7″>
<Attributes>
<Map>
<entry key=”requester” value=”spadmin”/>
<entry key=”source” value=”GroupManagement”/>
</Map>
</Attributes>
<ObjectRequest application=”AD” nativeIdentity=”CN=mydemo,CN=Users,DC=news,DC=com” op=”Delete” type=”group”/>
<Requesters>
<Reference class=”sailpoint.object.Identity” id=”4028818766902596016690272ffc010b” name=”spadmin”/>
</Requesters>
</ProvisioningPlan>
The group is also deleted from Active Directory.
1 Comment
Hi there,
why isn’t there a video for this topic? Pls upload the vide as well here. thanks